Using the Tor browser for navigating to the dark web network and wanting to protect your privacy online? You have come to the right place; here is everything you need on how to secure the Tor browser to protect your online activities from hackers and reduce the chances of being tracked.
How to Secure the Tor Browser
Tor browser is a secure stair to access the dark web as it offers privacy and anonymity. Moreover, in restricted countries, tor helps users to access free internet. However, the Tor browser has some security issues so it is not 100 percent secure. So here we have shared how to secure the Tor browser in detail for navigating the dark web.
Increase Tor Security Levels
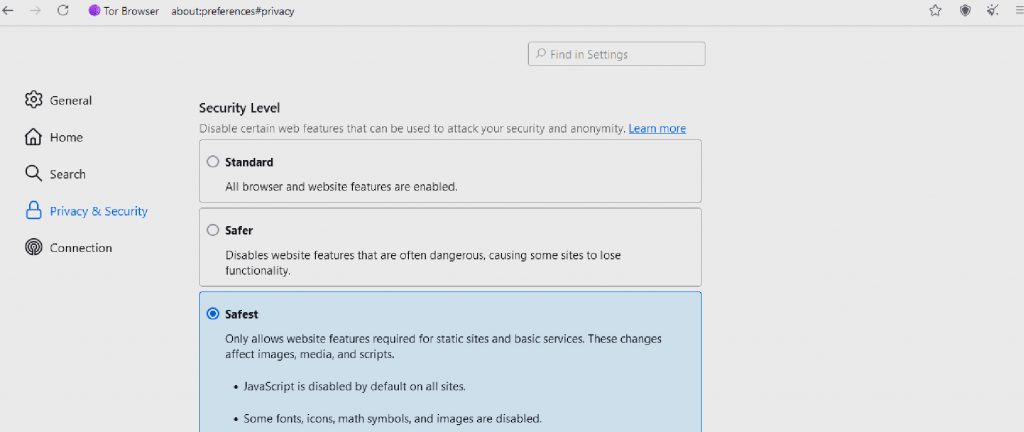
Tor Browser provides three security levels to its users, including
- Standard has all browser and site features turned on by default.
- Safer turns off JavaScript, some fonts, and math symbols on non-HTTPS websites. And HTML5 audio and video, and WebGL, become click-to-play.
- Safest turn off JavaScript, some fonts, icons, and math symbols on all websites. And HTML5 audio and video, and WebGL, become click-to-play.
The JavaScript on Tor can expose data since active content apps normally run with user account rights. It allows websites to track the user in ways Tor can’t protect the user’s identity and IP address. So disabling the JavaScript on the Tor browser restricts the user tracking by websites.
Follow these steps to increase the Tor browser security level.
- Open the Tor browser and click on the shield icon you will see at the top-right corner.
- Now click on the settings tab from the pop-up window.
- Select the safest option to increase Tor’s security level.
Use Tor Browser With a VPN
The entry nodes of the Tor network know the user’s IP while the exit nodes know where the user visited. However, the ISP might not know what the user is doing. But still tell the IP is connected to the Tor network. But when you use a VPN for Tor it helps address the security holes in the Tor network system. It shields your IP address from the entry nodes and your traffic from the exit nodes. So, using a VPN keeps your ISP and other snooping eyes from knowing that you are using Tor at all.
Use Antivirus Software
Many hidden onion links lead to illegal markets objectionable sites or malicious downloads. Hackers trick you into downloading malware or spyware that can negotiate your privacy. To stop this, run antivirus software on your system. It examines and deletes malware or viruses on your system and increases security levels.
Consider Using Linux Instead of Windows
Experts advise Tor users to use Linux instead of Windows for browsing Tor. Windows has many vulnerabilities and bugs. They will inject your system with malicious code or compromise your privacy. So, you would be more secure if you ran the Tor browser on the Linux operating system.
Update Tor Browser
Make sure your device operating system, Tor browser, and antivirus are up to date. The updated systems will save you from the latest detected vulnerabilities.
6 Safety Tips for Using the Tor Browser
Well, let’s clarify that since it is not 100 percent guaranteed when you are using Tor with the extra layer of security to your browsing. Thus, here are some safety tips that help you to stay safe and secure while using the Tor browser.
1: Use Tor Bridges
In many regions, the entry node traffic is blocked. Here you can connect to a bridge to get around these censorships. They look like regular traffic and don’t expose your connections to the Tor browser. Moreover, there is no complete list of bridges so if the ISP filters the connections to know the Tor relays, they can’t block them. Consequently, bridges add an extra layer of anonymity and prevent users from getting caught while connected to the Tor browser.
2: Access HTTPS Websites
HTTPS uses SSL (secure sockets layer) that encrypts and authenticates data going between a browser and a site. If you use HTTP, website exit servers can track your unencrypted traffic. And if malicious actors are operating them, they can steal your data. So, HTTPS websites are much more protected than HTTP websites. Keep in mind that you shouldn’t add your personal information to an HTTP site, whether it’s in the Tor browser or on the surface web.
3: Don’t Use P2P Protocol and Torrents
Tor Browser is not built for P2P file-sharing, and the exit nodes of Tor block the file-sharing traffic. However, torrent clients won’t typically encode your IP address, which could be shared with torrent trackers and peers. That’s how peer-to-peer file sharing on Tor can expose your identity. If you still download torrents, you compromise your anonymity and the speed of the Tor browser will be slow down.
4: Use a Secure Search Engine
Always use privacy-friendly search engines like DuckDuckGo instead of Google. If you want to explore the dark web or hidden onion links use Ahmia. It is on top of being a very precise privacy-focused search engine, and it also has blacklists sites that host offensive content.
5: Don’t Expose your Personal Data
Always avoid using your real email address, social network accounts, and anything that requires your information to keep your identity private. Tor Browser ensures your anonymity, but giving up your personal data on websites could straightforwardly render the browser useless.
6: Don’t Download Unknown Files
Hackers know that Tor is full of snooping and unsuspecting users. They may have laid many traps with viruses and malware. So don’t download anything from untrustworthy sources.
Sum Up
Of course, the tor can’t keep you completely safe which is why we have shared this blog with you. Once you know how to secure the Tor browser, you can easily access the dark web markets without worries. Securing the Tor browser with extra precautions is worth it for your privacy.